Public and Private Keys Explained

At the heart of cryptocurrency technology lies a powerful cryptographic system known as public-key cryptography. This system, built on the concept of key pairs, provides the foundation for security, ownership, and transactions in the blockchain world. This guide breaks down these crucial concepts in clear, accessible terms.
The Basics of Cryptographic Key Pairs
Public-key cryptography uses a pair of mathematically related keys to secure digital interactions:

These two keys work together through complex mathematical functions that are:

These two keys work together through complex mathematical functions that are:
- Easy to perform in one direction (creating a public key from a private key)
- Practically impossible to reverse (deriving a private key from a public key)
Private Keys: Your Most Valuable Secret
The private key serves as the ultimate proof of ownership in cryptocurrency systems:
What Exactly Is a Private Key?
A private key is:
- A long, randomly generated number (typically 256 bits in length)
- The cryptographic equivalent of a master password to your funds
- Something that should never be shared with anyone
Functions of a Private Key
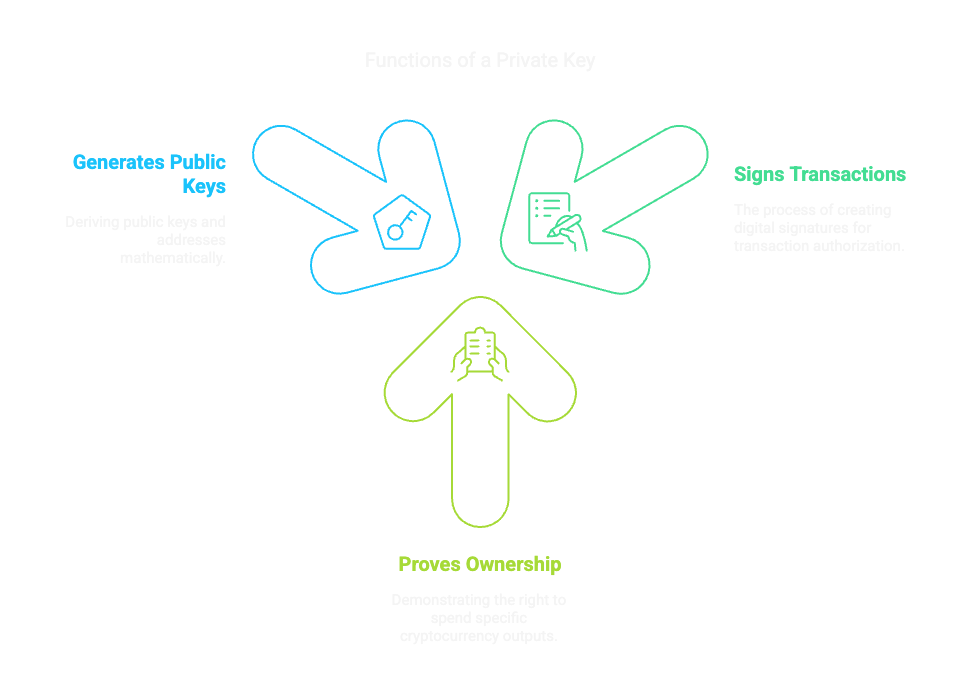
The Critical Importance of Private Key Security
The immutable nature of blockchain creates significant security considerations:
- No central authority can reset your private key if lost
- Transactions signed with your private key are irreversible
- Anyone who gains access to your private key can steal your funds
- Lost private keys mean permanently lost access to associated cryptocurrencies
Public Keys: Your Digital Identity
The public key is derived from your private key and serves as your identifiable address on the blockchain:
What Is a Public Key?
A public key is:
- A cryptographic code mathematically generated from your private key
- Something that can be freely shared without compromising security
Functions of a Public Key
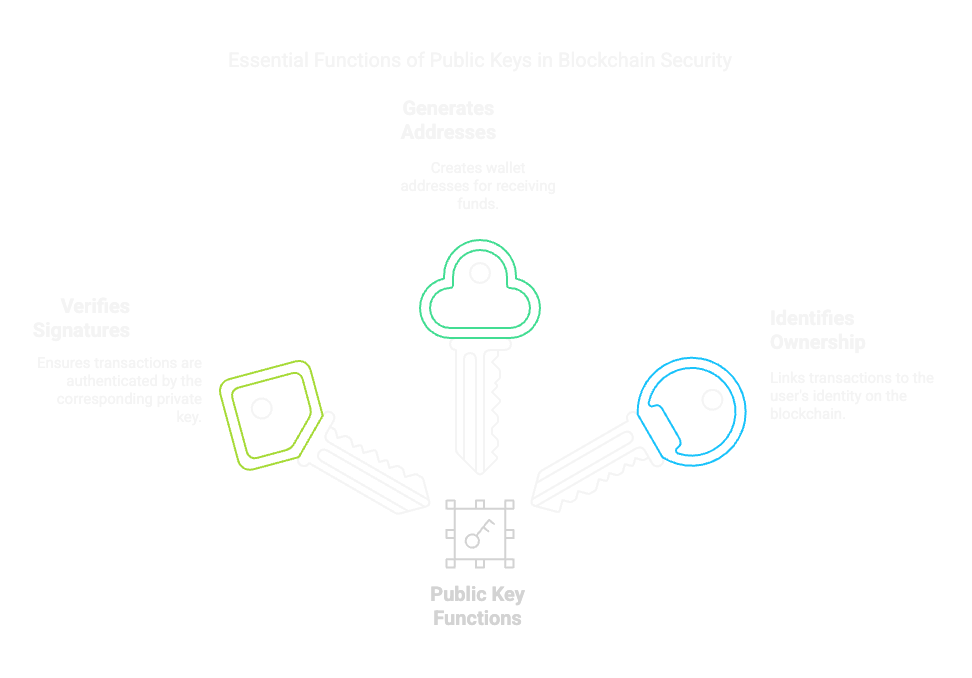
From Public Keys to Wallet Addresses
While you could use a public key directly as your receiving address, most blockchain systems create shorter, more user-friendly wallet addresses:
- The public key undergoes hashing algorithms
- Checksum data is added to help prevent typing errors
- The result is encoded to create the final address
How Key Pairs Work in Practice
Let’s walk through how public and private keys function in a typical cryptocurrency transaction:
Sending Cryptocurrency
When you send cryptocurrency to someone:
- You create a transaction specifying the recipient’s address and amount
- Your wallet software uses your private key to create a digital signature
- The transaction, including this signature, is broadcast to the blockchain network
- Network nodes verify the signature using your public key
- If valid, the transaction is added to the blockchain, transferring the funds
Advanced Key Concepts
As blockchain technology has evolved, several advanced key concepts have emerged:
Hierarchical Deterministic (HD) Wallets
HD wallets enhance key management through a structured derivation system:
- A single master seed generates an entire tree of key pairs
- New addresses can be generated without requiring new backups
- Different cryptocurrency assets can be derived from the same seed
Multi-Signature (Multisig) Keys
Multisig technology enhances security by requiring multiple private keys:
- Transactions require signatures from M of N possible keys (e.g., 2-of-3)
- Provides additional security for high-value wallets
Best Practices for Key Management
Effective key management is essential for cryptocurrency security:
Secure Storage Options
Consider these methods for storing private keys:
- Hardware wallets: Purpose-built devices like Ledger or Trezor
- Paper wallets: Physical documents stored in secure locations
- Steel backups: Metal plates resistant to fire and water damage
What to Never Do with Keys
Avoid these dangerous practices:
- Digital storage without encryption: Never store unencrypted keys on computers or phones
- Cloud storage: Don’t use cloud services for key backup without strong encryption
- Email: Never send private keys or seed phrases via email
Conclusion
Public and private keys form the cryptographic foundation that makes cryptocurrency possible. By understanding how these keys work together and how to properly secure them, you can participate in the cryptocurrency ecosystem with confidence. Remember that in the world of blockchain, you truly are your own bank—with all the freedom and responsibility that entails. Taking the time to implement proper key security measures is essential for protecting your digital assets.


